Is it a legitimate request or is it an online phishing scammer trying to gain access to your online account information?
Is there a definitive method that you can use to distinguish legitimate email requests from online phishing scams?
Take a peek at this (simply click on a photo to expand it):
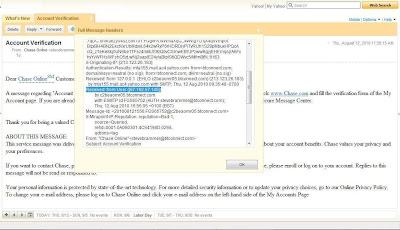
Here is an example of an email request I just received. Let's take a quick walk-through on some of the items that I look for to determine if an email is really a phishing attempt trying to gain personal account information.
First, notice that this email seeks to bypass all skepticism by leveraging:
- The name of a large and recognizable bank—Chase
- Implying that you need to perform some type of important action—account verification. Either you need to do it or someone has already attempted it and you need to check the veracity and integrity of your account.
Then it goes on to discuss the steps on how to verify your account information and how Chase values your business.
Here's what this message does right.
It's short. There is one line that describes what you have to do to verify your account. The rest of the message seeks to establish the credibility of the email by outlining how to contact Chase and stating how much they value you as a customer. All standard stuff that you can find at the end of any email from any big service provider.
Here's what makes this email stand out as a phishing email:
- It's not really from Chase. Yeah, it says that it's from Chase Online, but the actual sender is someone from btconnect.com. You know, if it's from Chase, it should say something like xxx@chase.com. Chase is big enough to have its own domain and its own army of servers.
- It's not to anyone. While the “From:” field has someone who is not from Chase, the “To:” field is empty. This is a tactic used by spammers and phishers to blast out emails to a large recipient list. It allows them to address the message to “Dear Chase Online Customer”.
Those are the easy identifiable signs that are enough to warrant a further investigation.
Now for the fun part.
If you suspect that you received a phishing email, first look at the full email headers. On Yahoo, you can get to the full header using the “actions” button and selecting the “View Full Header” option. This example is on my Yahoo! honeypot account.
In the window with the full header that pops up, we see a lot of undecipherable information which at first glance can be intimidating.
The highlighted section is the IP address of one of the mail servers. Running a search on the IP address through Google revealed a sight that tracks questionable activity called “Project Honeypot”:
Here we see that this site indicates that the IP address is associated with a machine that has the characteristics of a mail server, no surprise there:
Looking at another site reveals that the server is located in Great Britain. Again, no surprise since the service provider is btconnect.com where the “BT” stands for British Telecom.
The line in the header that we really want is this one, “Received from User [xxx.xxx.xxx.xxx]” This is the IP address the local service provider leased to the end user allowing them to gain access to the Internet.
As you can see, our “Chase” emailer was in San Antonio, TX using an expendable email account from British Telecom. This isn't surprising since spammers make use of free email addresses provided by Yahoo!, Google, and Hotmail all of the time. Spammers create phishing email addresses, use them and then flush them when they become compromised. You are never meant to return a message to these accounts. That's why there is typically another contact email address provided in the body text or they use the email to promote a phishing website to cull your information online.
Going back to the my email and looking at some of those Chase links, we see that they don't actually point to www.chase.com. They point to a file on the site hotelrandevy.com.
Anytime you have questions about the link in your email, hold your mouse over the link, but don't click it. The actual site address will appear in the status bar at the bottom of the browser. If it is not a place that you want to go, then don't click it.
So what does all of this mean to us?
Does it gives us the ability to really identify who sent us the email?
Not really.
The email information in the header can be manipulated, for example it identifies the sender as Chase.
The actual email address is expendable—any one of us can create the email address charliebrown123 on Google or Yahoo and start sending spam email out for the purpose of phishing.
The IP address is probably the only thing that the user can't manipulate, but with powerful laptops, reliable mobile computing and growing free WI-FI locations, the IP address can easily be from a Starbucks, McDonald’s, or an unsecured wireless router in a church. So we really don't know the location either (by the way, this last point makes it extremely important for you to secure your home wireless router unless you want to unknowingly participate in these kinds of activities).
So we are back to square one. We don't know who really sent the email.
But we do know something.
We know that the email is not from Chase and that it is phishing for personal information.
If you have an email that you suspect is not from who it says it's from, take a look at the full headers and then run a check on the IP address. You'll quickly determine if you should respond to the email or just delete it.
For another example on examining suspected phishing email, see my other post, Did You Get Phished By Chase?
Good Selling!







No comments:
Post a Comment